Third-Party Cybersecurity Risk Management — Updates for a Changing Risk Environment
by Ray Bolton, Cyber Risk Management Specialist, Supervision and Regulation, Federal Reserve Bank of Chicago, Jennifer Judge, Cyber Risk Management Specialist, Supervision and Regulation, Federal Reserve Bank of Chicago, and Patrick McAntire, Senior Community, Regional, and Specialty Bank Examiner, Supervision and Regulation, Federal Reserve Bank of Chicago
Third-party service providers are a fact of life in modern community banking. The range of services banks seek to outsource continues to grow as technologies evolve and the array of potential services continues to expand with the rise of financial technology, or fintech, partnerships. Outsourcing certain activities often provides a cost-effective alternative to hiring specialized in-house staff. However, the benefits of outsourcing these activities naturally come with added risk. Each new third party that is granted access to or resides on an internal network is a new vector through which a bad actor can attack and infiltrate the bank.
According to a recent report from the Ponemon Institute, an independent research organization focused on information security, 54 percent of the companies surveyed for the report have experienced a data breach caused by one of their third parties in the past year. Unauthorized network access was the most common root cause of these attacks, representing 40 percent of the discovered breaches.1 Not only is the number of breaches concerning, but the impact of these attacks has become more significant as well. In 2022, the level of breach impact almost doubled, with 4.73 affected companies per compromised vendor, compared with 2.46 affected companies per compromised vendor in 2021.2 A bank can have the most advanced network security equipment and configurations on the market, but if the issue comes from those who have been granted access to the network, then these otherwise effective security controls may fail to contain the risk. Fortunately, the implementation of strong controls has the potential to greatly reduce the success rate of attacks in this sector.3
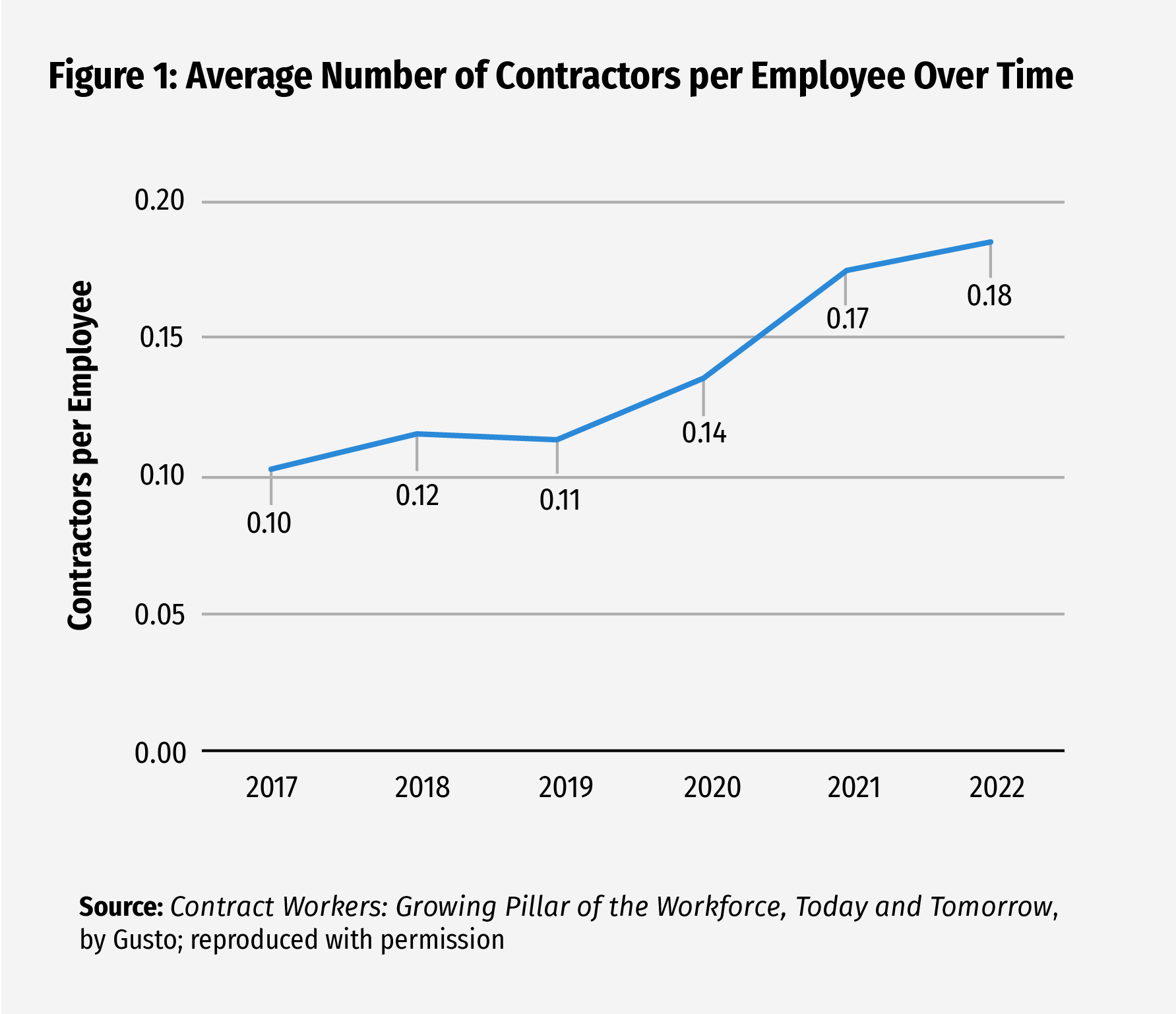
The proliferation of third-party relationships in banking heightens the need for strong third-party risk management. Community Banking Connections has provided a thorough look at this topic in the past; see “The Importance of Third-Party Vendor Risk Management Programs” from the first issue of 2017.4 Since 2017, banks’ reliance on vendors has grown. In fact, the ratio of contractors to employees at the average company has increased 63 percent since 2019 and is now nearly 1 to 5 (see Figure 1).5 The Federal Reserve and other regulatory agencies have recognized the increasing importance of this topic and recently published new guidance designed to help banks manage the risks of third-party relationships, including those with fintechs.6 This article highlights the key third-party cybersecurity risk management practices that may assist community bankers in mitigating the risks arising from these relationships and also highlights what to look out for when selecting new third-party partners.
Elements of a Strong Third-Party Risk Management Program
Third parties that hold a bank’s sensitive information present cybersecurity risks, as a breach can threaten sensitive customer information and the internal bank network. Banks are required to protect nonpublic customer information per the Gramm–Leach–Bliley Act,7 which includes information held by third parties. A cyber event at a third party may compromise a community bank’s customer information. While there is no set way to manage cybersecurity risks at third parties, a bank can implement a range of practices to bolster its third-party risk management program.
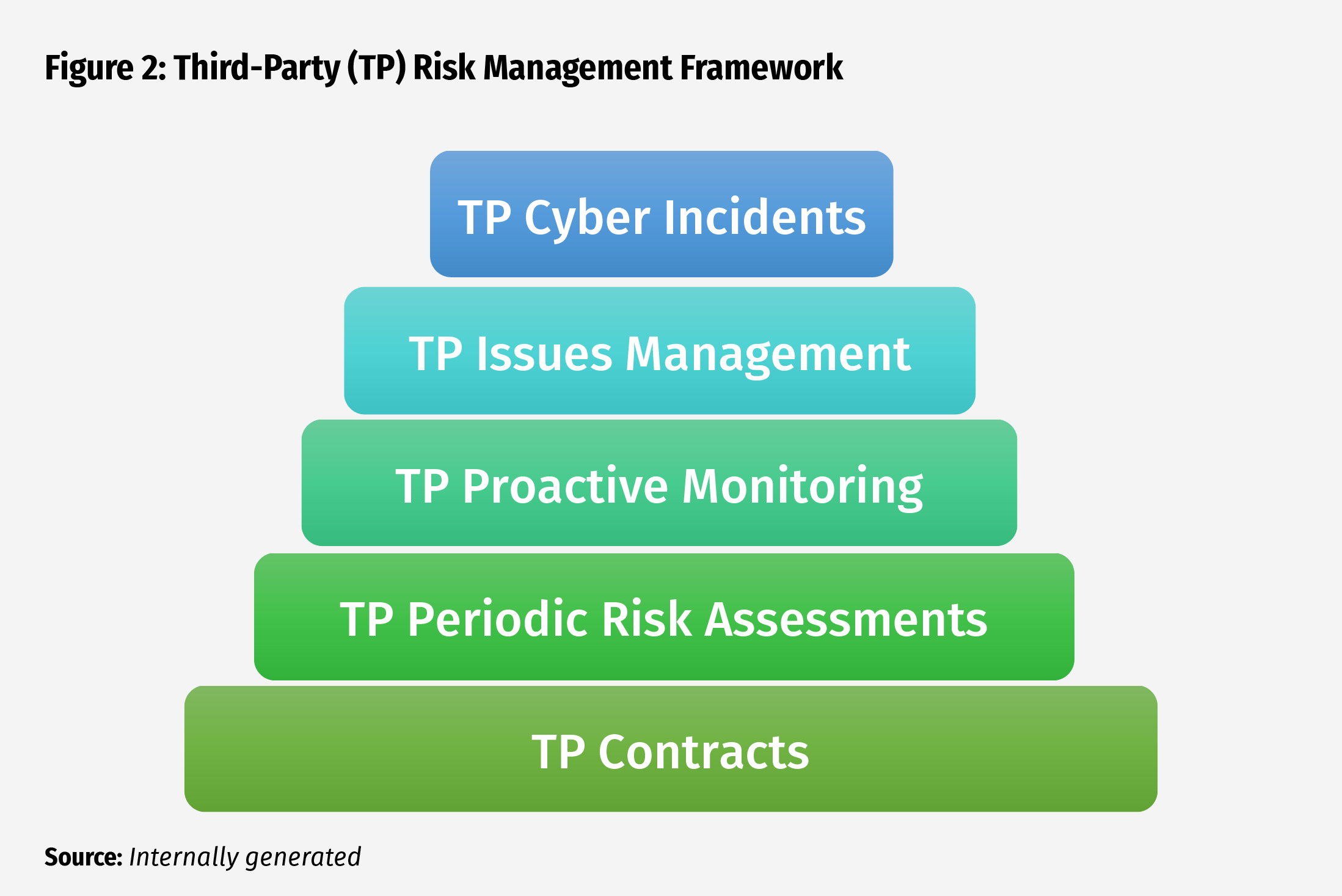
One way to consider these practices is to view the risk management framework as a “pyramid,” with a core foundational element upon which other control and monitoring practices are built (see Figure 2). The foundational element in this case is the contract, followed by periodic risk assessments, proactive monitoring, issues management, and cyber incident response planning. A collection of strong management practices for each block of the pyramid is presented for consideration in strengthening a community bank’s third-party risk management programs.
Contracts
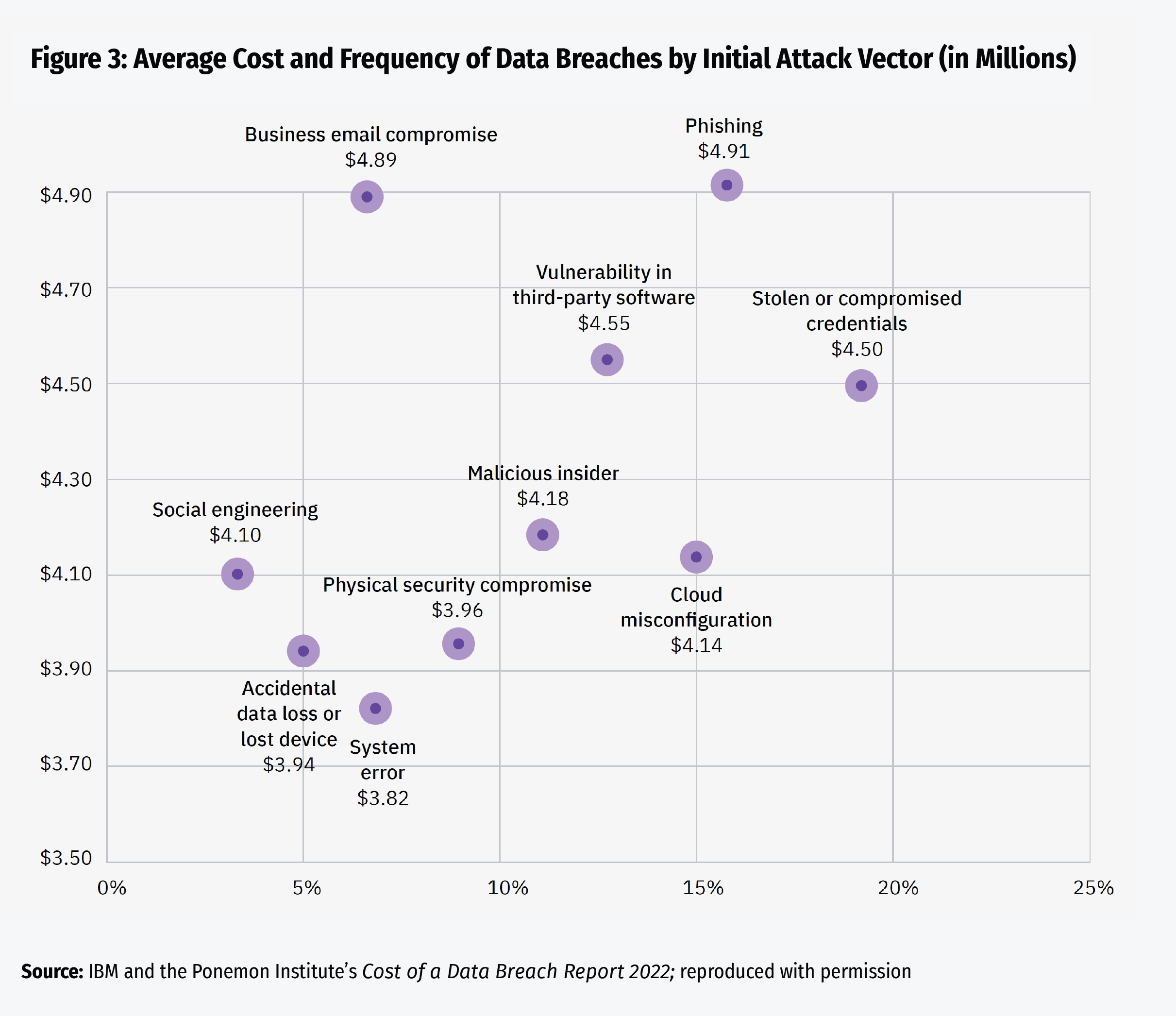
Contracts represent the foundation of a strong third-party risk management program. Community banks can use the contracting process to incorporate clauses requiring third parties to implement key cybersecurity controls into legally binding agreements. Management should ensure that contracts with third parties reflect the same level of cybersecurity protection expected within the bank, including contractual provisions such as requiring multifactor authentication, intrusion detection, or independent control reviews. Effective contracts generally include cyber awareness training for third-party employees because a significant portion of initial attack vectors involve compromised employee credentials or phishing schemes (see Figure 3).8 Common provisions community banks may use as a starting point for their own contract negotiations include requirements to provide detailed reports on any internal monitoring performed by the third party (i.e., ongoing audits), identifying a maximum timeline to report a data breach from the date of discovery,9 maintaining a cybersecurity program and policy, updating and testing the business continuity plan, and encrypting all critical data.
Risk Assessments
Community banks should develop a comprehensive risk assessment process that measures the level of risk presented by each third party. This process is known as the risk-tiering methodology and helps to accurately quantify the level of risk introduced by each third party. A strong risk-tiering methodology incorporates key cybersecurity considerations into the overall risk assessment. Some key considerations include how the third party connects to the bank, the associated level of cyber risk for each connection method, what bank resources and information are accessible, whether the third party allows employees to access bank data while working remotely, and any prior history of breaches. An effective risk assessment process also includes consultation with internal or external subject matter experts and, if possible, onsite audits. Management can remain well informed by leveraging the contract to ensure the bank is getting all the information and reports promised in a timely manner.
Proactive Monitoring
An additional aspect of strong third-party risk management is a robust oversight program that involves risk assessments coupled with appropriately frequent monitoring between risk assessments to ensure that the terms of the contract are fulfilled. Active monitoring between risk assessments assists in evaluating the day-to-day cybersecurity posture of third parties. Monitoring aims to address four key questions about the data that banks share with third parties:
- Who has access to the data?
- What type and volume of data are being shared?
- How is the information being shared?
- Where are the data stored?
Community banks may outsource the monitoring of their third-party vendors to yet another vendor. However, such arrangements do not diminish a bank’s responsibility to operate in a safe and sound manner and establish risk management practices to effectively manage the risks arising from its outsourcing activities. If a bank does contract with a third-party monitoring service, it is key that management understands the full capabilities of the service, including which vendors will be included in the program, how information about any discovered issues will be prioritized, how the information gathered will impact the vendor risk level within the risk assessment, and when alerts may trigger the incident response or business continuity plan.
Issues Management
A well-developed issues management process is a key aspect of strong third-party risk management. Certain third-party technology issues, such as control deficiencies or audit findings noted in a service organization control type 2 report, are inherently more complex to remediate, which further highlights the importance of a well-developed issues management process. Any issues or concerns identified during the third-party risk management review process should include information such as a description of the issue, the issue owner, the risk rating, the expected remediation timeline with an action plan, and any compensating controls. If the third party cannot or will not resolve the issue, bank management will need to take appropriate next steps, which can include terminating the relationship and hiring a new third party. If a bank is willing to accept the risk from an outstanding issue at a third party, management should provide a rationale for accepting the risk and keep the board of directors or a board-appointed committee apprised of such matters.
Cyber Incident Response
Data show that security-related incidents at third parties are a virtual inevitability. The most recent Data Breach Investigations Report published by Verizon notes that, of the 16,312 security incidents the team analyzed, 5,199 were confirmed data breaches.10 Managing a cyber incident with a third party will be more complex because banks are trying to understand and resolve issues that occur in an environment that they do not control. Strong incident management practices begin with developing a third-party cybersecurity incident playbook to address steps that will be taken to mitigate risk when an attack affects a critical third party. If a bank relies on a third party for technical expertise, it is important that the bank consults the third party when developing the playbook. Additional strong practices include creating and sharing (in advance) a collection of critical questions for third parties to quickly provide responses to the bank during a cyber incident, ensuring that contracts are reviewed during and after an incident to understand the bank’s rights around cybersecurity incidents, conducting an after-action review, and updating the incident response playbook as needed after an event has concluded.
Conclusion
Cyberattacks are an ever-present threat to community banks, and one of the most frequent vectors of infiltration is through third-party service providers, making a strong third-party risk management program increasingly important. A recent survey of members of the Financial Services Information Sharing and Analysis Center (FS-ISAC) showed that 52 percent of the respondents plan to make changes to their third-party risk management processes as a result of the current threat environment.11 SR letter 23-4, “Interagency Guidance on Third-Party Relationships: Risk Management,”12 intends to promote consistency in third-party risk management guidance and to assist banks in identifying and managing the associated risks.
Third-party service providers can offer many benefits to community banks, from new market segments to cutting-edge financial technologies to heightened network management expertise and more, but each new party within a technical system creates additional risk for a bank to manage. The practices presented throughout this article aim to help community bankers strengthen their third-party risk management programs and better secure their networks and customer information in an increasingly connected environment.
|
Additional Resources
|
- 1 See the Ponemon Institute’s September 2022 study, The 2022 Data Risk in the Third-Party Ecosystem Study, available at https://tinyurl.com/mu24nkpf.
- 2 For more information, see the Third Party Breach Report released by Black Kite, available at https://blackkite.com/wp-content/uploads/2023/01/third-party-breach-report-2023.pdf.
- 3 For more information, see Verizon’s 2023 Data Breach Investigations Report, available at www.verizon.com/business/resources/T9e/reports/2023-data-breach-investigations-report-dbir.pdf.
- 4 The article is available at www.cbcfrs.org/Articles/2017/I1/third-party.
- 5 For more information, see the November 2022 report from Gusto, Contract Workers: Growing Pillar of the Workforce, Today and Tomorrow, available at https://gusto.com/wp-content/uploads/2022/11/Contractors-in-the-Modern-Workforce_General-Report_Q2FY23-.pdf.
- 6 See Supervision and Regulation (SR) letter 23-4, “Interagency Guidance on Third-Party Relationships: Risk Management,” available at www.federalreserve.gov/supervisionreg/srletters/SR2304.htm and SR letter 23-7, “Creation of Novel Activities Supervision Program,” available at www.federalreserve.gov/supervisionreg/srletters/SR2307.htm.
- 7 For more information, see the Federal Trade Commission’s web page on the Gramm–Leach–Bliley Act, available at www.ftc.gov/business-guidance/privacy-security/gramm-leach-bliley-act.
- 8 For more information, see Cost of a Data Breach Report 2022 from IBM and the Ponemon Institute, available at www.ibm.com/downloads/cas/3R8N1DZJ.
- 9 The average time between an attack and the disclosure date was 108 days in 2022. See Black Kite’s Third Party Breach Report.
- 10 See Verizon’s 2023 Data Breach Investigations Report www.verizon.com/business/resources/T9e/reports/2023-data-breach-investigations-report-dbir.pdf.
- 11 For more information, see the FS-ISAC report, Annual Cyber Threat Review and Predictions, available at www.fsisac.com/hubfs/NavigatingCyber-2022/NavigatingCyber2022-TLPWHITE-FIN.pdf.
- 12 See SR letter 23-4.
